Creating
a Password: The user first selects three people that is familiar to him
(e.g., boss, coworker, brother, father, friend, etc…). The user then randomly
selects a random action and a random object (using a computer program for
random selection). The user should store the names of the people he selected
publically in a convenient location (file on the computer, public web site,
printed photo carried in wallet etc…). The user does not need to worry about
hiding these names. He should also publically note which account the names are
being linked to.
Memorize
Password: The user spends a few moments trying to imagine the stories
playing out.
Rehearse
Password: Rehearse the password after 1 day, then after 4 days, then
after 8 days, 16 days ….(logging in to the site counts as a rehearsal.)
Recall
Password: The user looks at the names, remembers the corresponding
actions/objects and enters his password.
Recommendations: Use
a small set of vivid actions and vivid objects (around 80 actions + 80
objects). The user should use separate names/PAO stories for each account.
Example Password
Creation: The
user first picks three people with whom he is familiar (e.g., I picked Manuel
Blum, Anupam Datta and Stephen Rudich). The user then generates an action and
an object to go with each person to get three stories: “Anupam Datta kissing
piranha,”

“Stephen
Rudich destroying shark”
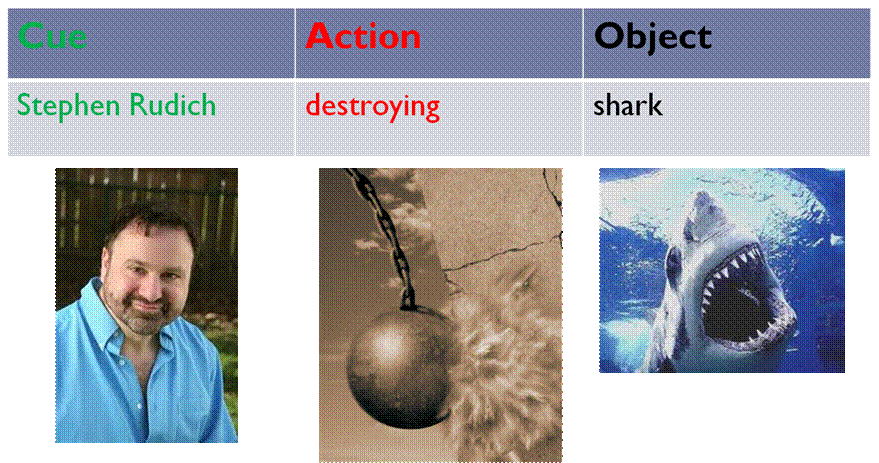
and “Manuel Blum torturing lion.”
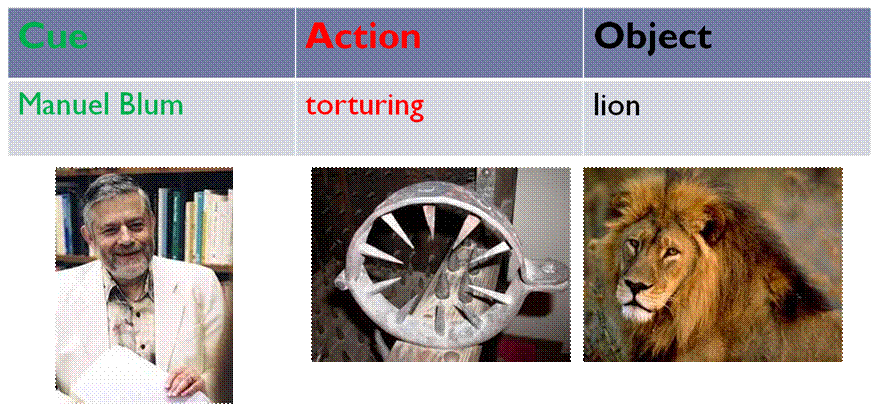
I
spent a few moments thinking about each of these stories. I would write down
the public cue (Amazon.com: Anupam Datta, Stephen Rudich and Manuel Blum). The
actual password is kept private.

Security Analysis: If used correctly this password management scheme is highly secure! An
adversary who has seen multiple passwords will most likely fail to crack your
passwords. There are around 377,149,515,625 passwords that an adversary would
have to guess before he recovered your password. This is true even if
1) The adversary knows how
you are picking your passwords.
2) The adversary has seen the
names that you are using as cues.
3) The adversary knows the actions
and objects that are in your set.
Actions:
sewing
gnawing
mowing
rowing
oiling
egging
waving
bowing
seizing
stewing
signing
searing
bribing
swallowing
sucking
saving
sipping
tazing
tattooing
drying
dueling
dodging
tugging
taping
nosing
hunting
numbing
inhaling
knifing
nipping
muddying
mooning
miming
marrying
mauling
mashing
mugging
moving
mopping
racing
riding
reeling
reaching
raking
raping
lassoing
welding
aligning
leashing
elbowing
juicing
shining
sheering
judging
choking
chipping
goosing
coating
concealing
destroying
kissing
flaming
kicking
punching
canning
combing
gluing
cooking
giving
copying
vising
voting
fanning
fuming
firing
flying
fishing
voguing
high fiving
pissing
batting
burying
plowing
puking
popping
Objects:
saw
teacup
hen
ammo
arrow
owl
shoe
cow
hoof
boa
sauce
suit
snow
pirahna
chainsaw
shark
tiger
snake
razor-blade
sumo
seal
sock
safe
soap
daisy
toad
dime
tire
dish
duck
dove
ant
onion
wiener
nail
navy
menu
mummy
hammer
mail
microphone
horse
rat
iron
ram
rolling pin
roach
rib
lion
lime
leach
lock
leaf
cheese
jet
chain
chime
gyro
chili
jeep
goose
cat
wagon
igloo
couch
cake
coffee
cab
vase
foot
phone
waffle
fish
fag
bus
patty
bunny
bomb
bra
pill
bush
bike
beehive
puppy